Policers monitor traffic flows and identify and respond to traffic violations. For example, policers can monitor TelePresence flows at the campus access edge. Because TelePresence flows are bounded (to typically 5 Mbps per screen at 1080p), flows in excess of such bounds would be indicative of network abuse and can be immediately identified and responded to by policers.
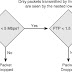
Policers achieve these objectives by performing ongoing checks for traffic violations and taking immediate prescribed actions when such violations occur. For example, a policer can determine if the offered load is in excess of the defined traffic rate and then drop the out-of-contract traffic, as illustrated in Figure 1.
Additionally, policers can re-mark excess traffic to identify (but not necessarily drop) traffic that exceeds a given traffic contract, which might be valuable for reporting, billing, or capacity planning purposes. In such a role, the policer is called a marker. Figure 2 illustrates a policer functioning as a marker.
Cisco IOS policers are modeled after token bucket algorithms. Essentially, these algorithms are metering engines that keep track of how much traffic might be sent to conform to the specified traffic rates.
A token, in everyday use, is an item given to an individual that represents the right to use a given service, such as to ride on the subway or to play a video game, and so on. In QoS terminology, a token permits the policing algorithm to send a single bit (or in some cases, a byte) of traffic. Typically, these tokens are granted at the beginning of a second, according to the defined policing rate, referred to as the Committed Information Rate (CIR).
Tokens granted at the beginning of each second of operation are placed in a logical cache, referred to as the bucket. A key difference in policing algorithms is how unused tokens are dealt with at the end of each second: Some policers allow unused tokens to accumulate in the bucket, whereas others force unused tokens to be discarded. These differences, and the effects on traffic policing, is discussed in more detail shortly.
For example, if the CIR is set to 8000 bps, then 8000 tokens are placed in the bucket at the beginning of each second. Each time a bit of traffic is offered to the policer, the bucket is checked for tokens. If there are tokens in the bucket, the traffic is passed. One token is removed from the bucket for each bit of traffic that is passed, and such traffic is viewed to conform the rate, and the specified action for conforming traffic is taken. (The conforming traffic is typically transmitted unaltered.) When the bucket runs out of tokens, any additional offered traffic is viewed to exceed the rate, and the exceed action is taken. (The exceeding traffic is either re-marked or dropped.)
In addition to defining the CIR, policers require that a committed burst (Bc) also be defined. The committed burst, also known as the normal burst, refers to the bytes allowed in a subsecond traffic burst before packets will be considered to exceed the rate limit.











No comments:
Post a Comment