The Single-Rate Three-Color Marker/Policer presented a significant improvement for policers, in that it made an allowance for temporary traffic bursts (if the overall average transmitted rate was equal to or below the CIR). However, the variation in the amount of accumulated excess burst credits could cause a degree of unpredictability in traffic flows. To improve on this, a Two-Rate Three-Color Marker/Policer was defined in RFC 2698. This policer addresses the Peak Information Rate (PIR), which is unpredictable in the RFC 2697 model. Furthermore, the Two-Rate Three-Color Marker/Policer allows for a sustainable excess burst (negating the need to accumulate credits to accommodate temporary bursts).
The Two-Rate Three-Color Marker/Policer uses the following parameters to meter the traffic stream:
- PIR: Peak Information Rate; the maximum rate traffic ever allowed
- PBS: Peak Burst Size; the maximum size of the first token bucket (referred to as Be within Cisco IOS syntax)
- CIR: Committed Information Rate; the policed rate
- CBS: Committed Burst Size; the maximum size of the second token bucket (referred to as Bc within Cisco IOS syntax)
- Tc: Token count of EBS; the instantaneous number of tokens left in the CBS bucket
- B: Byte Size of Offered Packet
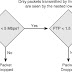
The Two-Rate Three-Color Policer also uses a two-token bucket algorithm, but the logic varies slightly. Rather than transferring unused tokens from one bucket to another, this policer has two separate buckets that are filled each second with two separate token rates. The first bucket is filled with the PIR amount of tokens, and the second bucket is filled with the CIR amount of tokens. Any unused tokens are discarded (from both buckets) at the end of each second. In this model, the Be works the same as the Bc, except for the PBS bucket (not the CBS bucket). This means that Be represents the peak limit of traffic that can be sent during a subsecond Interval. The logic varies further in that the initial check is to see if the traffic is within the PIR, and only then is the traffic compared against the CIR. (That is, a violate condition is checked for first, then an exceed condition, and finally a conform condition, which is the reverse of the logic of the previous model.) Figure 1 illustrates this logic.
The Two-Rate Three-Color Marker allows for sustainable excess bursts (and is not dependent on accumulating credits) and has a hard-top peak limit, as shown in Figure 2.
Example 1 shows the configuration to police traffic on class-default to a CIR of 256 kbps with a Bc of 1500 bytes and a PIR of 512 kbps with a Be of 3000 bytes. Note that for this policer, CIR and PIR are defined in bps, but Bc and Be are defined in bytes. As before, the policer is configured to function as a marker that complies with the Assured Forwarding PHB, but this time for AF class 4.
Example 1: RFC2698 Two-Rate Three-Color Policer Example
Router(config)# policy-map RFC2698-POLICER Router(config-pmap)# class class-default Router(config-pmap-c)# police cir 256000 bc 1500 pir 512000 be 3000 Router(config-pmap-c-police)# conform-action set-dscp-transmit af41 Router(config-pmap-c-police)# exceed-action set-dscp-transmit af42 Router(config-pmap-c-police)# violate-action set-dscp-transmit af42